Manufacturers Guide to Becoming a Cybersecurity Champion
Organizations can improve cybersecurity resilience by following these common-sense steps
Most small and mid-sized US manufacturers rely on information technology to run their business. Whether from shop, assembly, network-connected machines, primary systems like MRP, financial and HR, or employees using their own devices in a Bring Your Own Device (BYOD) strategy, data is the critical life blood of every company.
It's easy to think that the Small & Medium-sized Business (SMB) market isn't necessarily a target for cyber criminals, but according to a 2021 Verizon Data Breach Investigations report, the number of small business breaches with confirmed data disclosure increased as a portion of the total to 46% from around 27% in 2020.
A January 2022 World Economic Forum (WEF) study suggests that the lack of SMB cyber resilience is seen as a critical threat to supply chains, partner networks and systems. Digitization has increased during the COVID-19 pandemic, and the increased inter and remote connectivity has opened up more threat vectors and put "the global population into a new trajectory" of risk.
We can glimpse the impact of a world where the flickering flames of digital transformation have slowly built into a sizable inferno. Verizon DBIR 2021
84% of WEF respondents shared that cyber resilience is considered a business priority in their organization with support and direction from leadership, and a smaller, but significant proportion (68%) see cyber resilience as a major part of their overall risk management. 88% of respondents indicate that they are concerned about the cyber resilience of SMBs in their ecosystem.
Manufacturing replaced financial services as the industry with most IBM Security X-Force "remediated attacks" in 2021 at 23.2% of the total. In a breakdown of top attack types, ransomware was the second highest category, behind a combined group that included Distributed Denial of Service (DDoS), adware, cryptominers and fraud. In attacks against six industries that rely on operational technology (OT), manufacturing was the primary target with 61% of the incidents. Across all industries, email phishing and Business Email Compromise (BEC) is still the top infection vector at 41% of the total.
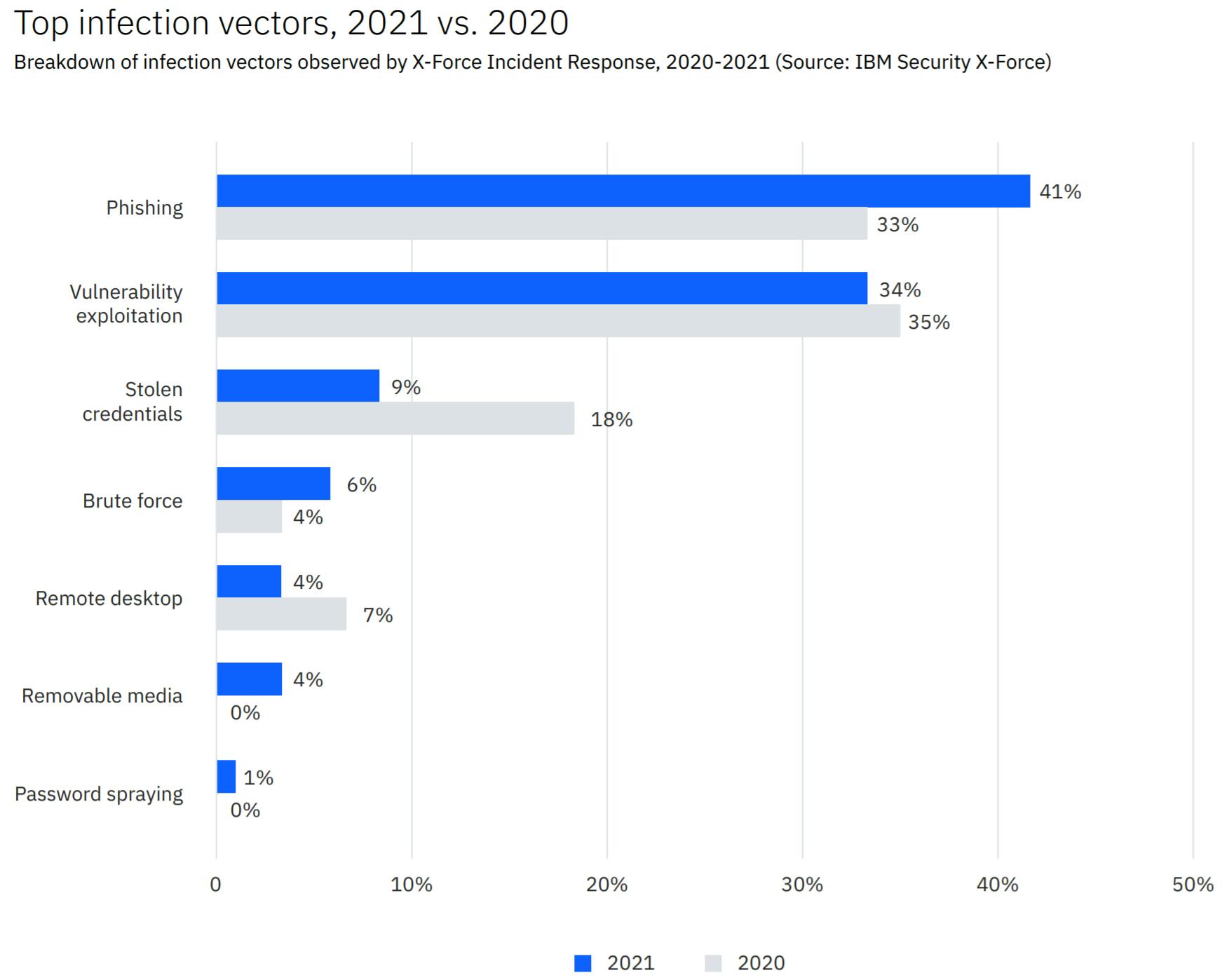
Cyber attacks on all businesses are becoming more frequent, targeted, and complex: according to a Nov. 2021 Accenture report, there were on average, 270 attacks per company last year, a 31% increase over 2020. And it's not just direct attacks, third-party risk continues to be a concern as successful breaches to organizations through the supply chain have increased from 44% to 61%.
The good news is that cybersecurity is starting to be seen as an organizational priority, as investment, from boardrooms to the federal government, continues to rise. The Accenture report describes four broad organizational levels related to cybersecurity resilience, and business strategic alignment. These levels range from organizations with weak resilience, termed "Vulnerable", to those that are "Cyber Champions", with strong programs and mature practices.
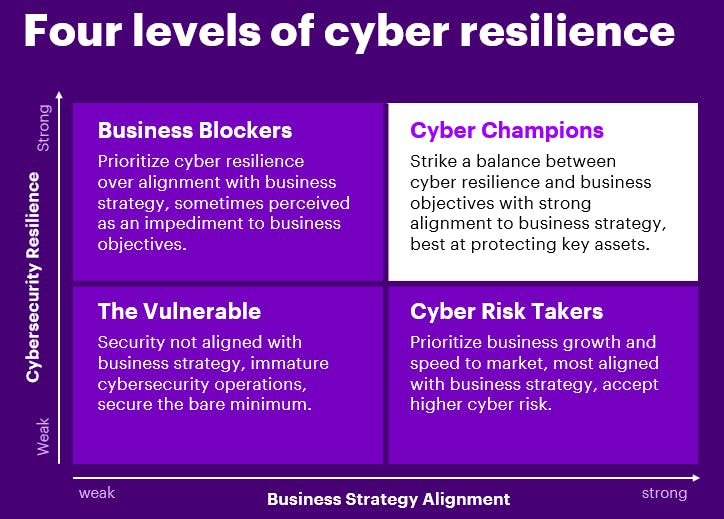
Cyber Champions
Cyber Champions focus on business enablement, striking a balance between proactively protecting organizational and customer data, while ensuring process throughput with a customer-focused value stream. Cyber Champions as a group, tend to stop more attacks, find and fix breaches faster, and reduce breach impacts.

And while championing cybersecurity can require a sustained level of effort, cybersecurity can be a key market differentiator. Protecting sensitive customer information inspires trust, and shows customers that their data and business is valued.
At a high level, organizations can be more like Cyber Champions by doing things like ensuring that someone within the organization is focusing on cyber security, and that they have a seat at the table for setting direction and deciding organizational priorities. Leadership should also work to strengthen and align security with business objectives using a security framework and tracking associated metrics. If this expertise isn't available in-house, partnering with external professionals and tapping into industry associations can bridge the gap. One way to do this, is to seek peer recommendations, and connect with cybersecurity professionals on LinkedIn.
Ultimately security is a shared responsibility across the organization. It should be aligned with business priorities, and integrated into any internal software development life cycle.
Five Sensible Steps To Improve Cyber Resiliency and Become a Cyber Security Champion
Organizations that find themselves on the lower left-hand side of the cyber resilience quadrant, can begin their improvement journey by thinking about cyberscurity in five common practice areas. These five areas are articulated in a security framework created by the National Institute of Standards and Technology (NIST). NIST is a non-regulatory agency commissioned in 1901. NIST created the Cybersecurity Framework (CSF) in 2014 following an executive presidential order, with a goal of developing a set of standards, guidelines, and best practices. The goal of the CSF is to reduce cyber risks and help organizations build, strengthen, and manage their cybersecurity program.
The framework describes the five practice areas in a continuum that helps organizations identify and protect critical assets, work to detect and respond to malicious events, and plan for ways to recover. While following the NIST CSF guidelines can help manufacturers become more resilient, as with all process improvement efforts, becoming a Cyber Security Champion is not a one-time event, but a continual, ongoing set of activities.
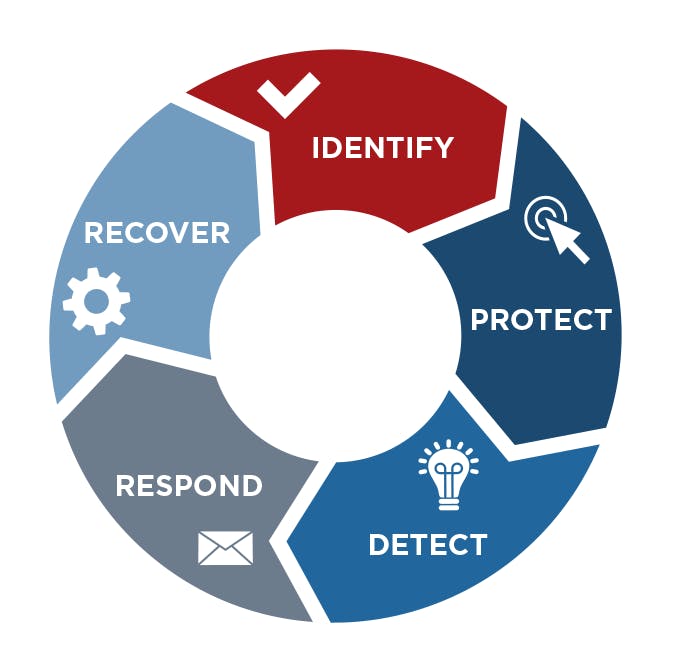
The five CSF practice areas follow:
Identify
Think about managing cybersecurity risks to systems, people, assets, data, and capabilities. Identify where your most critical data exists - where is it located or stored, and in which systems.
- Identify who has access to this information, including associated user accounts and privileges.
- Require individual user accounts for each employee.
- Start working on policies and procedures for information security that lets employees know what is acceptable and non-acceptable behavior.
Protect
Limit or contain the impact of a potential information or cybersecurity event.
- Limit employee access to data and information: for instance, don't allow a single individual to both initiate and approve a financial transaction.
Use the principle of least privilege: resource and system accounts should allow only the access needed for the employee to do their job.
Install surge protectors and Uninterruptible Power Supplies (UPS) to avoid damage from power changes.
- Regularly patch operating systems and applications to keep them safe.
- Install and activate software and hardware firewalls on your business networks.
- Secure your wireless access point and networks.
- Set up web and email filters to reduce malware and email spam.
- Train your employees as part of the on-boarding process, and periodically thereafter to help them understand vulnerabilities and threats to business operations.
Detect
Proactively review system and network logs to allow timely discovery of information or cybersecurity events.
- Install and update anti-virus, anti-spyware, and other anti-malware programs.
- Maintain and monitor logs: firewalls, systems, and anti-virus software normally track events in activity logs. These logs should be reviewed frequently for evidence of potential threat events. Logs should also be backed up and saved for at least one year. Timely log analysis may be a tall order for many small and medium businesses, so consider outsourcing this work to a third party. There are many "Managed" or "Extended" detection and response offerings by well-known third parties.
Respond
Develop a plan for the immediate actions you will take in case of a fire, medical emergency, burglary, natural disaster or cyber incident, including roles and responsibilities, the process to follow and how to secure your information and systems. Remember that the first and primary responsibility of any business is to protect human life. Systems can be replaced, humans can't.
Recover
The recover function helps an organization resume normal operations after an event.
- Ensure full backups of important business data and information.
- Schedule automatic incremental data backups (in other words, changes in data since the last backup).
- Consider cyber insurance: similar to other types of insurance, cyber insurance may help you respond to and recover from a security incident. This type of coverage is getting more difficult to obtain. Be prepared to answer detailed questions about your cybersecurity program during the application process!
Get Going!
Although cyber attacks on the SMB market are increasing, Cyber Champions focus on business enablement, and striking a balance between meeting organizational mission, vision, and values, while proactively protecting critical assets and data. Use the NIST Cybersecurity Framework and Identify, Protect, Detect, Respond, and Recover practice areas to help organize and guide your journey to become a stronger Cybersecurity Champion, and make your manufacturing business more cyber resilient.
